Disclaimer: The steps described below have only been tested in a lab environment.
Note: To set up an Oracle Cluster File System on Oracle Linux, see my previous article, see this URL.
This article explains how to mount an Oracle Cluster File System when the SELinux status on enforcing mode.
Tables of contents:
- SELinux
- Mount OCFS2 while the SELinux status on enforcing mode
1. SELinux:
SELinux is a security enhancement to Linux which allows users and administrators more control over access control.
Access can be constrained on such variables as which users and applications can access which resources. These resources may take the form of files. Standard Linux access controls, such as file modes (-rwxr-xr-x) are modifiable by the user and the applications which the user runs. Conversely, SELinux access controls are determined by a policy loaded on the system which may not be changed by careless users or misbehaving applications. For more information, see this URL.
a- SELinux Modes
SELinux runs in one of three modes.
- Disabled: The kernel uses only DAC rules for access control. SELinux does not enforce any security policy because no policy is loaded into the kernel.
- Permissive: The kernel does not enforce security policy rules but SELinux sends denial messages to a log file. This allows you to see what actions would have been denied if SELinux were running in enforcing mode. This mode is intended to used for diagnosing the behavior of SELinux.
- Enforcing: The kernel denies access to users and programs unless permitted by SELinux security policy rules. All denial messages are logged as AVC (Access Vector Cache) denials. This is the default mode that enforces SELinux security policy.
b- SELinux Context
Under SELinux, all file systems, files, directories, devices, and processes have an associated security context. For files, SELinux stores a context label in the extended attributes of the file system. The context contains additional information about a system object: the SELinux user, their role, their type, and the security level. SELinux uses this context information to control access by processes, Linux users, and files. For more information, see this URL.
2- Mount OCFS2 whiles the SELinux status on enforcing mode:
After setting up an Oracle Cluster File System, and configuring the file /etc/fstab for permanent mount.
Step 1: For permanent OCFS2 file system mount.
Configure the SELinux to enforce mode, by editing the file /etc/sysconfig/selinux.

Step 2: Troubleshooting SELinux.
SELinux log messages are labeled with the “AVC” keyword so that they might be easily filtered from other messages, as with grep.
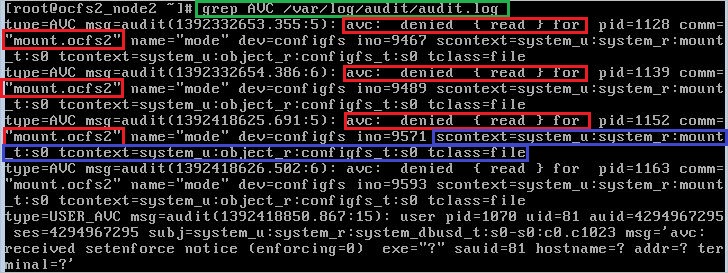
Step 3: Install the package SELinux Troubleshooting.
SELinux Troubleshooting tool can be used to help analyze log files converting them into a more human-readable format.
# yum install setroubleshoot setroubleshoot-server
Step 4: Use the tool sealert.
It acts as the user interface to the setroubleshoot system, which diagnoses and explains SELinux AVC denials and provides recommendations on how to prevent such denials.
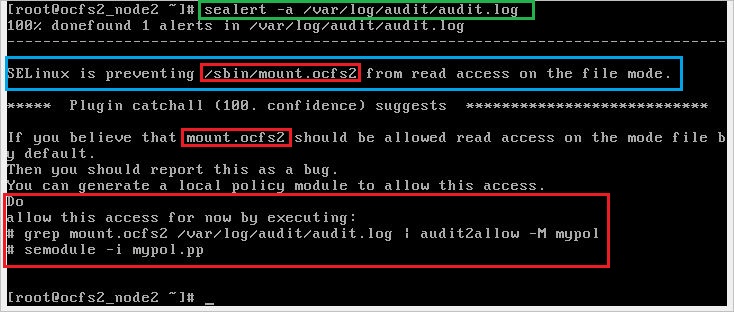
Step 5: Generates SELinux policy allow_audit rules from logs of denied operations.

Step 6: Manages SELinux policy modules.
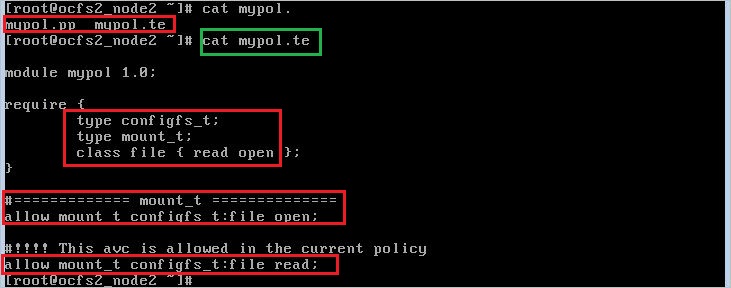
We then load our mypol policy module using the ‘semodule’ command into the current SELinux policy:
# semodule –i mypol.pp
Step 7: Remount your OCFS2 file system.
# mount –a
Note: Now mount your Oracle Cluster File System under SELinux on enforcing mode.
Conclusion:
This article explains how to mount an OCFS2 file system while SELinux on enforcing mode.
To set up an OCFS2 on Oracle Linux, see my previous article.













